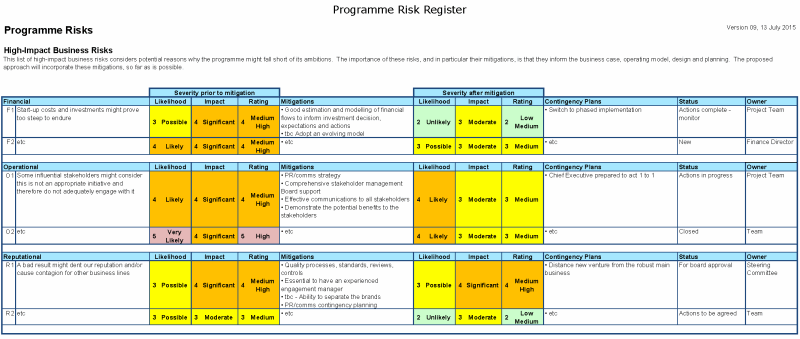
SANS class: SEC 401 Security Essentials Bootcamp Style Assessment: GIAC GSEC 3 Credit Hours ISE 5101 is the introductory, technicallyoriented survey course in the information security engineering master's program. It establishes the foundations for designing, building, maintaining and assessing security functions at the enduser, network and enterprise levels of an organization. The Food Security Information Network (FSIN) is a global initiative cosponsored by FAO, WFP and IFPRI to strengthen food and nutrition security information systems for producing reliable and accurate data to guide analysis and decisionmaking. FSIN serves as a neutral technical platform for exchanging expertise, knowledge and best practices, developing harmonized methods and tools, and. NIEM is a common vocabulary that enables efficient information exchange across diverse public and private organizations. NIEM can save time and money by providing consistent, reusable data terms and definitions and repeatable processes. Netand our affiliates proudly follow the IEEE Code of Ethicsand the 2 Code of Ethics. Since 1977, our companies, and since 1995, the All. Net Web site, have provided indepth information presented in a direct manner. We hope that our site is both informative and enjoyable and we welcome your feedback. Share The Importance of Building an Information Security Strategic Plan on Twitter Share The Importance of Building an Information Security Strategic Plan on Facebook. Information Technology Laboratory Computer Security Resource Center Computer Security Resource Center Computer Security Resource Center In military theory, strategy is the utilization during both peace and war, of all of the nation's forces, through large scale, longrange planning and development, to ensure security and victory (Random House Dictionary). The father of Western modern strategic study, Carl von Clausewitz, defined military strategy as the employment of battles to gain the end of war. The 32nd International Workshop on Global Security was presented in Paris at the Hotel National des Invalides in November, 2015 with the Ptronage of French Defense Minister JeanYves Le Drian. The workshop was organized in partnership with the Center for Strategic Decision Reseach, the Institut des hautes etudes de defense nationale (IHEDN) within the Prime Minister's organization, NATO. McGrawHill Homeland Security Handbook: Strategic Guidance for a Coordinated Approach to Effective Security and Emergency Management, Second Edition [David Kamien on Amazon. FREE shipping on qualifying offers. Featuring a foreword by Michael Chertoff, former Secretary of Homeland Security, The McGrawHill Homeland Security Handbook The Government of Canada Strategic Plan for Information Management and Information Technology sets information, data and technology direction for the Government of Canada and identifies enterprisewide priorities and key activities for departments, agencies and service provider organizations for the next four years. With over 40, 000 students, 5 campuses and research that's solving the problems of the world, there's a lot going on at our university. If you can't find the answer you're looking Cybersecurity consulting and secure development services. We help our clients to prepare for cyberattacks by understanding and managing cyberexposure, enabling them to make informed decisions and to put pragmatic and effective protection in place. Learn about our cybersecurity consulting services, including strategic advisory, program development and risk management, controls and compliance assessments, and adversarial security testing. The White House Office of Management and Budget (OMB) is proposing for the first time in fifteen years revisions to the Federal Government's governing document establishing policies for the management of Federal information resources: Circular No. A130, Managing Information as a Strategic Resource. More specifically, Circular A130 provides general policy for the planning. Measuring and Managing Information Risk: A FAIR Approach [Jack Freund, Jack Jones on Amazon. FREE shipping on qualifying offers. Using the factor analysis of information risk (FAIR) methodology developed over ten years and adopted by corporations worldwide New Zealand takes an active role in peace, human rights and security initiatives, advocating for rules that curb armed conflict, halt the spread of dangerous weaponry and. Information security, sometimes shortened to InfoSec, is the practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information. The information or data may take any form, e. Information security's primary focus is the balanced protection of the confidentiality, integrity and availability of data. The information security industry is high stakes and always changing. There is immense responsibility to protect information in an everchanging landscape of cyber security risk, and leaders know that an event could be catastrophic to companies, customers, and careers. The following pages provide a preview of the information contained in. COBIT 5 for Information Security. The publication provides guidance to help IT and Security professionals The following six elements of strategic planning are the keys to successful strategic planning: simplicity, passion (emotional energy)speed of planning and adapting, connection to core values, core Competencies, communication, and implementation. From Security Strategy: From Requirements to Reality by Bill Stackpole and Eric Oksendahl. Bellevue University's Master's in Strategic Finance prepares professionals to be strategic leaders in corporate finance, mergers and acquisitions, enterprise, insurance, and banking. From its establishment as a one man start up in London, Global Strategies Group (GLOBAL) quickly grew from a strategic risk consultancy for government and commercial organisations, to providing a comprehensive range of strategic and operational support in challenging environments, including physical security services, training and capacity building, aviation security and complex logistics. Recent years have seen an increase in attacks against state representatives, notably the police, across Germany. Some perpetrators of those attacks have been found to represent an ideology that opposes the state and its representatives and, more specifically, considers. In delivering IT security consulting services to large enterprises in Australia, particularly in the health care, utility and large government sectors, Information Systems Group has used the International Organization for Standardization (ISO) standards extensively, for example ISO for security and ISO for IT service management..